Zero Trust moves from buzz-word to practical approach as enterprises seek to secure their business
We’ve heard a lot about Zero Trust over the years, but the onset of the COVID-19 pandemic moved the buzz word abruptly to the forefront. In part, due to the rapid increase in demand for digital workplaces for remote work, and in part to a rapidly evolving threat landscape, the topic quickly captured C-Suite mindshare.
Providing hardware is the easy part…
Enabling employers with required endpoint hardware is the easy part. The far greater challenge is to protect the company and its assets against growing cyber crime and to limit the risks associated with the steep rise in exposure points in information systems that are increasingly open and shared with an ecosystem of suppliers, customers, and third-party services.
…but ensuring secure access is a much bigger challenge.
But as this ecosystem and landscape grows in scale and complexity, so do the challenges in securing it. The solution is a significant shift in approach, one where organizations do not automatically trust devices or users inside or outside its perimeters and instead must verify any access request to its systems before granting access.
This approach – called a zero trust network - is built upon five fundamental design principles:
-
The network is always assumed to be hostile.
-
External and internal threats are always assumed to exist on the network at all times.
-
Network locality is not sufficient for granting trust in a network.
-
Every device, user, and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many sources of data as possible.
The efficacy of Zero trust approaches rely on important tools including security information management, advanced security analytics platforms, security user behavior analytics, and other analytics systems to help security experts monitor in real-time what is happening on their networks so they can act accordingly.
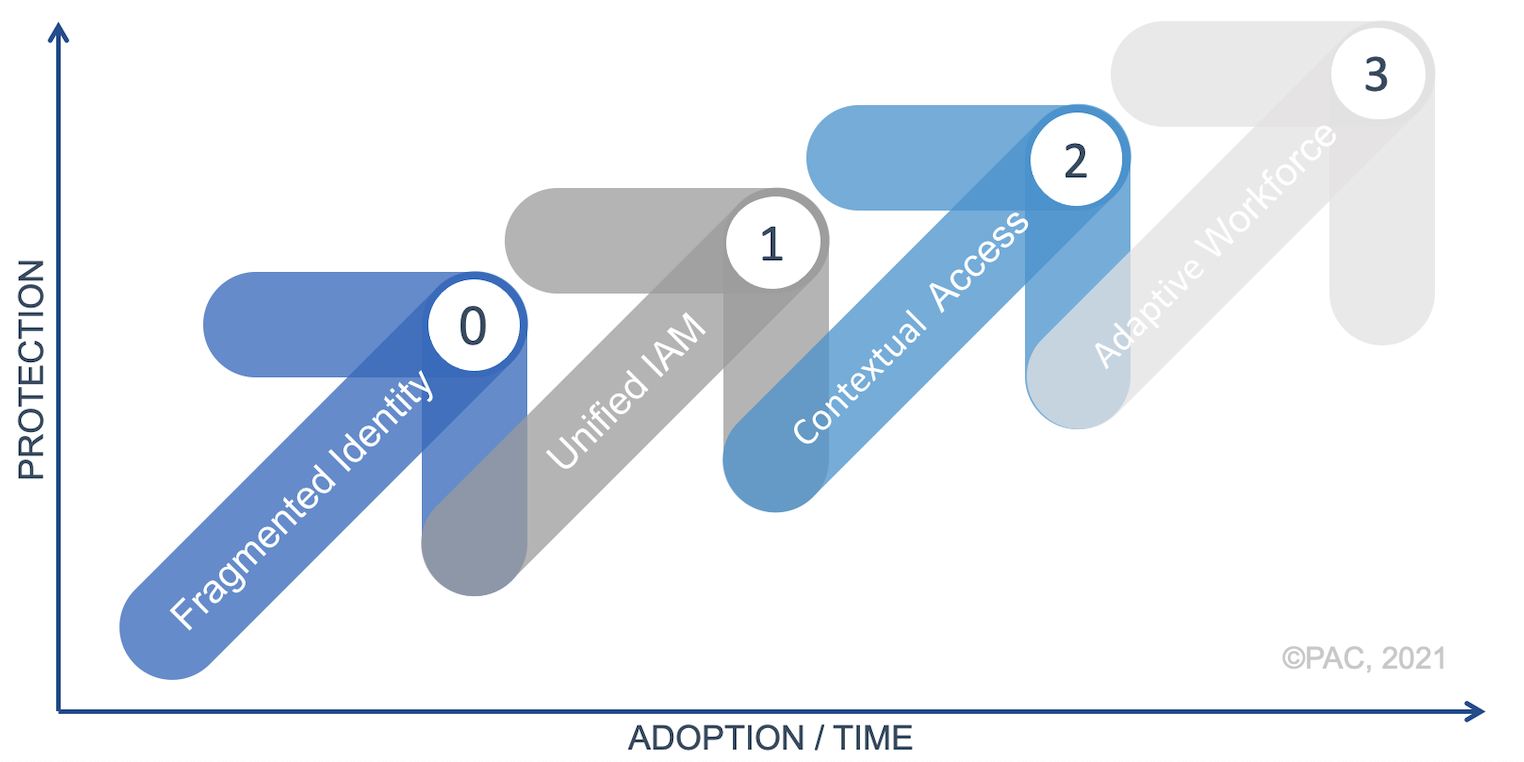
The Zero Trust journey
Of course, implementing a zero-trust network isn’t a simple process. To implement zero trust, organizations need time and usually external support, often following a common 4-stage approach:
-
Stage 0: Many organizations start their zero trust projects with on-premise directory services in a hybrid infrastructure, forcing IT to manage different identities across systems as well as applications and services that may be used without awareness of the IT department. For users, this means many passwords which are often unsecure.
-
Stage 1: To solve these identity issues, the next step would be Unified Identity and Access management including all systems (on- and off-premise) and applications, and obviously, all users.
-
Stage 2: the next stage in zero trust security is the use of context-based access policies. This means collecting the user’s context information (i.e. who is the user?), application context (i.e., which application the user is trying to access), device context, location / network, and applying access policies based on that information. A policy could be established to allow access by managed devices, but unmanaged devices logging in from never-seen locations would be prompted for a sort of multi-factor authentication.
- Stage 3: In the final stage, organizations extend the focus onto authenticating and authorizing access. This means that authentication no longer occurs only at the first access request, but continuously throughout the user’s experience through a continuous, adaptive, risk-based evaluation to identify potential threats during the user’s journey. In other words, if access to a system or application is granted, but the user does anything unusual, further authentication methods are used and access might be revoked.
Got stuck? You are in good company...
Without a doubt, zero trust is an important architecture principle to secure data access, but it is a complex endeavor. Most organizations are currently stuck between stage 1 and 2 and really need help to get to reach the secure utopia of stage 3.
…you can get there with a little help
Zero trust in combination with SASE and micro-segmentation elevates security to the next level, but such projects are complex. In almost all cases, organizations need external help from experts in designing such an infrastructure solution – whether from a vendor or independent consultants. Many of the leading IT Services firms are building out security-focused delivery capabilities that embed zero-trust approaches into solutions and services. So the good news is, for enterprises who are stuck on their journey to zero-trust, there is a dynamic marketplace for of solutions and expertise ready to support them.
What we expect
As the space evolves, PAC expects to see strong market demand for zero trust and even greater demand for the whole package (zero trust, SASE, micro-segmentation), as well as for security-focused consulting and solutions over the next 36+ months – as enterprises look to secure their sprawling operations, and push back against a rapidly evolving threat landscape.
Get more insights
Obviously Zero trust is not just a hype, there is a genuine need for enterprises to adopt a new security posture, pushed further by the need for digital workplaces. And of course, it is not the only next big thing in Cyber Security – to find our more, check out our trilogy of InBrief Analysis reports in which we cover the most relevant Cyber Security topics and technologies for users and service providers, explain the pros and cons, who should be interested and give advice how to handle it.
0 thoughts on "Zero Trust moves from buzz-word to practical approach as enterprises seek to secure their business"