Micro-segmentation – How organizations can reduce the attack surface to secure their business
COVID-19 marked a global increase in demand for digital workplace solutions, to power the necessary shift to remote working. The side effect of this trend is the growing dependence on digital technology and the subsequent increase in exposure points for IT systems. A fact that placed CISO’s and cybersecurity professionals in the spotlight as enterprises pushed them to urgently secure systems and mitigate risk.
A positive development from this is the maturing in enterprises outlook – they now understand that a more intelligent approach is required across data management and security in order to limit the risks linked to new ways of working.
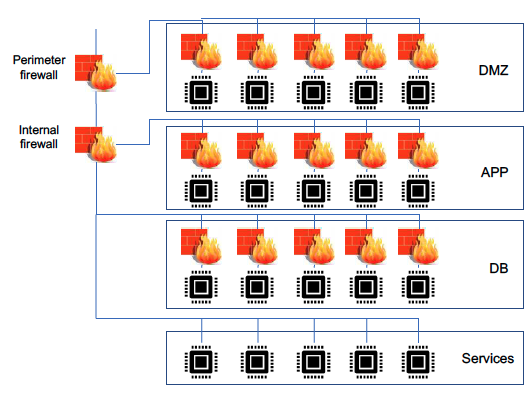
Crucially, with the realization that perimeter security is no longer sufficient, especially in a hybrid infrastructure that is to be securely integrated into an ecosystem, the idea of micro-segmentation is becoming increasingly important – with the topic quickly moving up the agenda of IT decision-makers.
The idea behind micro-segmentation is simple: Reduce attack surface
The evolution begins by reconsidering the role of perimeter security – which instead of its historical view as a protective wall covering the whole of an enterprises infrastructure, should instead be viewed as a collection of smaller pieces (for example, on-premise data center, cloud services, and ecosystem partner infrastructure building blocks). These pieces can vary between single data centers and single virtual machines or containers. Indeed, other perimeter definitions may be single applications.
The approach enables enterprises to develop the strategic position that there might be breaches which need to be handled, but a single breach must not be able to have a potential effect on the whole infrastructure, but only on a smaller part. In other words, micro-segmentation is designed to reduce the scope of damage of a single breach.
The most important elements of a micro-segmentation architecture are:
-
Persistence: even though data center topologies are constantly changing, the enforcement of provisioned security for a workload remains consistent despite changes in the environment.
-
Ubiquity: to provide an adequate level of defense, security management needs to depend on a high level of security being available to every system in the infrastructure. Micro-segmentation makes this possible by embedding security functions into the data center infrastructure itself.
-
Extensibility: New threats or vulnerabilities are exposed, old ones become inconsequential, and user behavior is the unstoppable variable that constantly surprises security management
Micro-segmentation – complex but safer
To manage micro-segmentation in a hybrid infrastructure, SDDC (Software Defined Data Center) approaches are commonly used. The integration of applications from different segments is particularly critical as on one hand the east-west traffic needs to be controlled (otherwise the micro-segmentation approach is meaningless) and on the other hand the data must be able to flow. This is why micro-segmentation and zero trust are often seen in combination.
Micro-segmentation in a nutshell
Simply put, the core tenets of the approach are:
-
Micro-segmentation limits the scope of damage of a single breach.
-
Micro-segmentation needs an SDDC solution in order to be practical.
- Micro-segmentation in combination with zero trust and SASE elevates security to the next level, but such projects are complex and need, in almost all cases, external help from professional services support in designing and implementing a zero trust, SASE, microsegmented infrastructure solution, whether from a vendor or independent consultants.
Over the next three years, we expect to see a strong and growing market for micro-segmentation and even greater demand for the holistic security packages that include zero trust, SASE, and micro-segmentation solutions, as enterprises grapple with the unique business environments created as a result of the COVID-19 pandemic.
Get more insights
There is a genuine need for enterprises to adopt a new security posture, pushed further by the need for digital workplaces. You can see more of our analysis on the latest trends in the Cyber Security in our trilogy of InBrief Analysis reports in which we cover the most relevant Cyber Security topics and technologies for users and service providers, explain the pros and cons, who should be interested and give advice how to handle it.